Password and Security Settings
Manage
The Security Settings
Toin editOPSCOM provide administrators with critical tools to enforce robust password policies and manage login security settings,for hoverall administrative accounts. Properly configuring these settings is essential for protecting sensitive system data, preventing unauthorized access, and complying with organizational security standards.
Security settings are managed within the System Settings area of OPSCOM.
- Hover over System
ConfigConfiguration, and click System Settings. - Click Security.
in the list of settings.The Manage System Settings window will
openopen, displaying all available security configurations.
In System Settings, click
Using this Feature
The Security component within System Settings allows administrators to configure various aspects of password management and allaccount thelockout security settings will be available.policies.
Password Security Settings
-
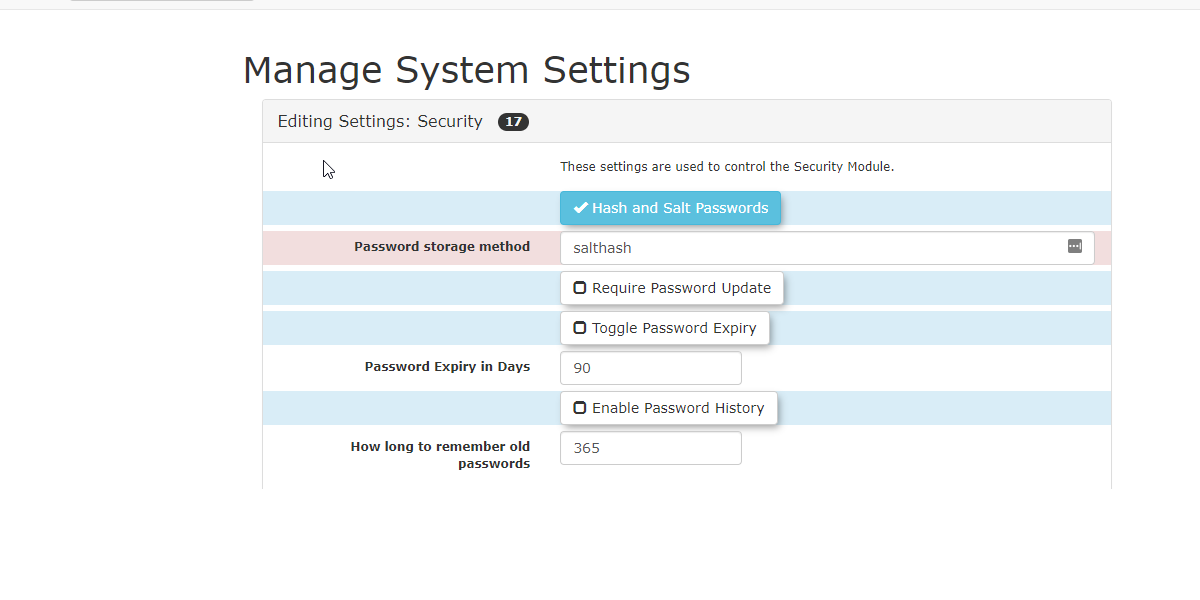
Salted Password
Hashing,Hashing:Password- Purpose:
ToggleThisPassword Expiry and Enable Password History
Update,Usingsalted password hashingsetting adds anextraessential layer of security to stored passwords. Hashing is a one-way, irreversible process thattakes the passwordconverts auseruser'senters and converts itpassword into a unique, short hash value.Salting"Salting"randomizesintroducesthea random stringofintodigitsthisforprocess,the hash value soensuring that even if two users have the same password,theytheir stored hash values willhavebedifferentdifferent.hashThisstrings.preventsIt"lookup"is not possible to(reverseengineerengineering)a hash, so you cannot “look up” whatof the originalpassword was. Instead, a user who forgets theirpassword,formeaningexample,forgottenwouldpasswordshavemusttoberesetreset,itnotcompletely.retrieved. This significantly limits anadministrator’administrator's ability to viewtheemployee passwordsof employeesand closesupaacritical security vulnerability. - Purpose:
Note: Once Hash and Salt is enabled, it should not be turned off.
-
Require Password Update:
-- Purpose: When activated, this setting
will forceforces users to change their passwordsonupon their next login. - Use Case: Ideal for ensuring compliance with regular password changes or after a password reset by an administrator.
- Purpose: When activated, this setting
-
Toggle Password Expiry:
-- Purpose: By
defaultdefault, passwords in OPSCOM do not expire.addedenhanced security, it isgoodbest practice tohavemandatepasswordsregularexpirepasswordeverychanges.90Thisdays.settingYouenablescantheenteruse of password expiry. - Configuration: Toggle this setting On.
- Password Expiry in days: Enter the number of days
beforeafterawhich an administrator's passwordexpirywilltoexpire,conformaligning with your organization's security policyand(e.g.,toggle90itdays).
on. - Purpose: By
-
Enable Password History:
-- Purpose: When toggled
on,On, OPSCOM will remember passwords previously used by an administrator. The system will then prevent the reuse of those passwordsyouforhaveausedspecified period. - Configuration: Set How long to remember old passwords (in days) to define the
past,durationandforwillwhich old passwords are notallowallowedrepeattousebeofreused.
thepassword - Purpose: When toggled
Password Strength and Admin Lockout Requirements
Using Password Strength Settings the admin can set rules for how complex a password needs to be to meet security rules.
These settings include:allow you to enforce complexity rules for administrator passwords.
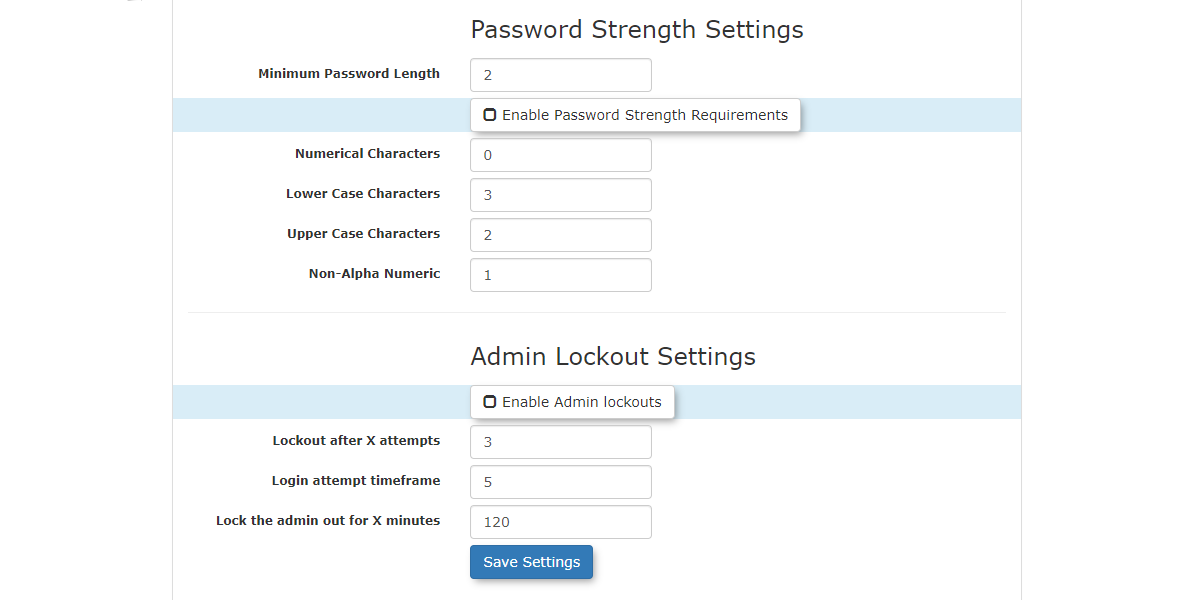
- Minimum Password Length:
-Sets the minimum number of charactersinrequiredtheforpassword
a password. - Enable
PasswordpasswordStrengthstrengthRequirementsrequirements-: Toggles on or off the following specific complexity requirements:- Numerical
: Sets the minimum number ofMinimumCharactersNumerical Charactersnumbers required in thepassword - Lower
: Sets the minimum number ofMinimumCase CharactersLowerlowercaseCase Characterscharacters required in thepassword - Upper
: Sets the minimum number ofMinimumCase CharactersUpperuppercaseCase Characterscharacters required in thepassword - Non-Alpha
: Sets the minimum number ofMinimumNumericNon-Alphanon-alphanumericnumeric(special)Characterscharacters required in the password (Speciale.g.,characters such as!, &, #,etc.).
- Numerical
Admin Account Lockout Settings
AdminsThese cansettings optprovide to set upan additional security settings that can lock the user outlayer of thesecurity systemby iflocking an incorrect password is entered repeatedly within a specific time frame. In the setting example, 120 minutes would lock the Adminadministrator out of their account after repeated incorrect password attempts.
- Enable Admin Lockouts: Toggles on or off the account lockout feature.
- Lockout after X Attempts: Sets the number of failed login attempts with an incorrect password before the system will lock out the administrator.
- Login attempt timeframe: Sets the timeframe (in minutes) during which incorrect login attempts are counted. For example, if an administrator fails 3 times within a 5-minute period, their account will be locked out.
- Lock the admin out for X minutes: Sets the duration (in minutes) that the administrator's account will remain locked. For example, setting it to
120 minuteswould mean the administrator is locked out for 2hours,hoursifbeforethreeanotherfailedloginattemptsattempt is permitted.
Best Practices & Considerations
- Robust Security Policy: Always implement a robust security policy that combines strong password requirements (length, complexity), password expiry, and lockout mechanisms.
- Enable Hashing: Ensure Salted Password Hashing is always enabled for maximum password security.
- Regular Password Expiry: Enforce regular password expiry (e.g., every 90 days) to
logmitigate the risk of compromised credentials. - Meaningful Lockout Settings: Configure lockout settings to balance security with user convenience. Too aggressive settings can lead to frequent lockouts, while too lenient settings can be a security risk.
- Communication: Inform administrators about the security policies in
occurplace,duringincludingapasswordfivestrengthminuterequirements,period.expiry rules, and lockout procedures. This helps them comply and understand why they might be locked out. - Admins can see, only OPSCOM Team can change: Several security settings (e.g., Hash and Salt, Require Password Update, Toggle Password Expiry, Enable Password History, Enable password strength requirements, Enable Admin Lockouts) are visible to administrators but can only be changed by the OPSCOM Team. For modifications to these specific settings, contact OPSCOM Support.