Configuring Multi-Factor Authentication on the User Portal
Introduction
Multi-Factor Multi-factorAuthentication authentication, or MFA,(MFA)auser user’saccounts account.in OPSCOM, significantly enhancing protection against unauthorized access. Currently, the onlyprimary method of MFA implemented is usingthe use of one-time passwords (OTPs) sent via email. This article outlines how administrators can configure MFA at the system level and how users interact with this enhanced security feature on their portal.
One-TimeSetup Passwords& Configuration
TheImplementing one-timeMFA passwordinvolves isadministrator-side aconfiguration randomly-generatedwithin passwordSystem thatSettings isand sent tocustomizing the userassociated withinemail an email. The password must be entered into the website after the regular login before the user is able to access their account.template.
Admin Side Configuration
One-time passwords will not be available on athe websiteuser portal until it is enabled within systemSystem settings.Settings.
System settings are located in the menu:
- Hover
over System Configuration
→and click System Settings
The relevant setting can be found under:
User Profile
→tab click the Enable Multi-Factor Authentication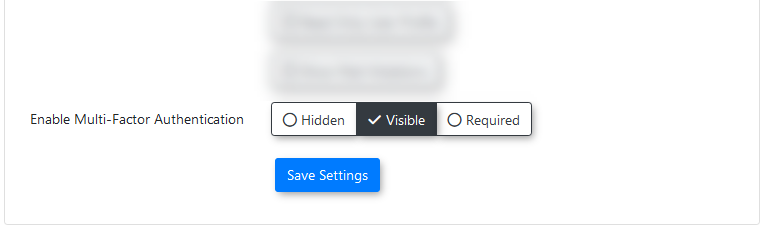
If MFAthis setting withinis thenot systemavailable settings.for you to change, please have your primary Admin contact support@ops-com.comcom to have it turned on.
ItThis is a ternary setting,setting, withmeaning 3it has three different states:states, allowing for flexible control over MFA implementation:
Email Template Configuration
The content of the one-time password email that is sent to userusers is defined within thea associateddedicated email template.
Email templates can be found under the headings:
- Hover
over System Configuration,
→Content & Designs→and click Email Templates
Here,
administrators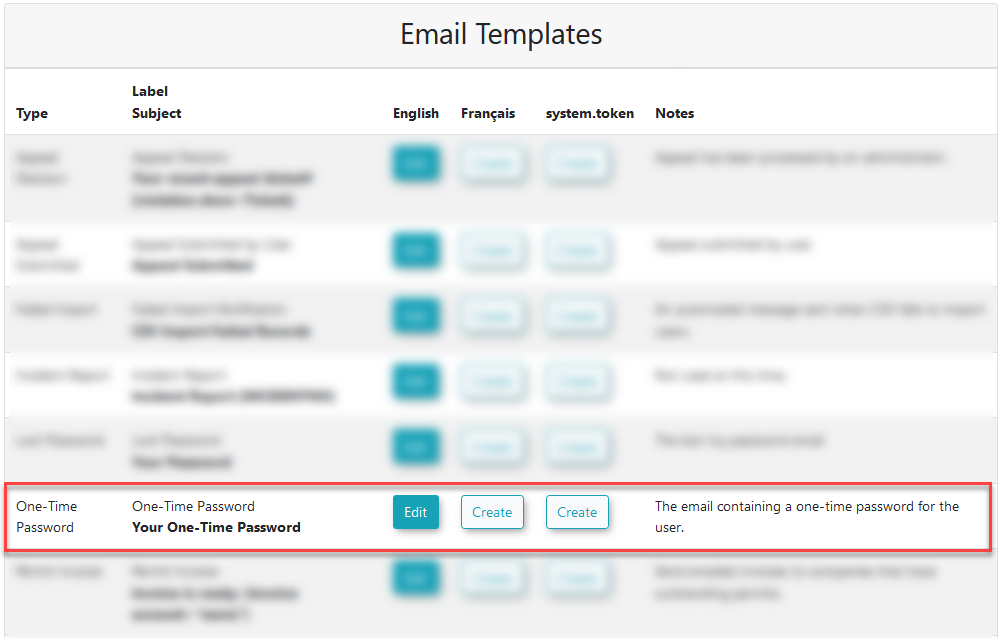
The contentbranding of the emailemail. can be defined here.
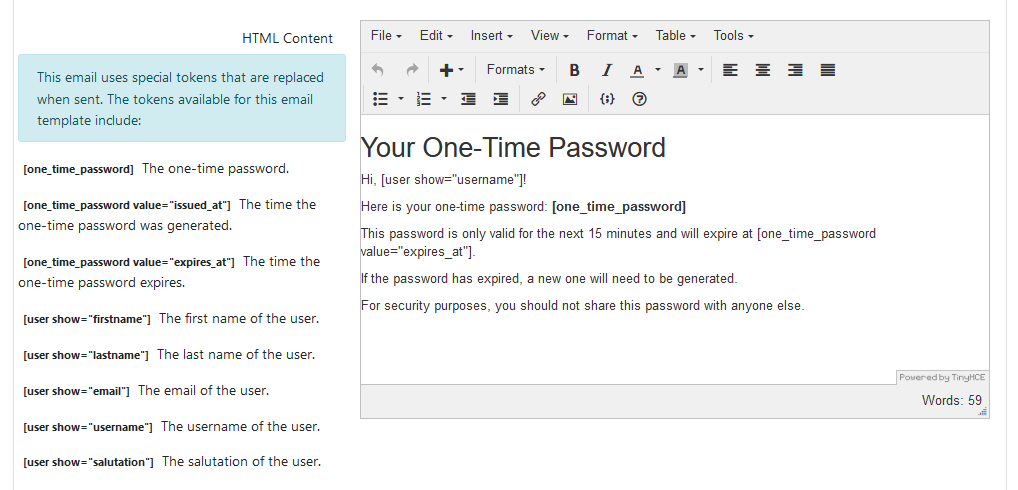
In addition to the general user-specific shortcodes, the one-time password emailthis template has a number of one-time passwordincludes specific shortcodes relatedfor toOTP it.details:
The one-time password specific shortcodes are:
[one_time_password]:TheInserts the randomly generated one-time password.[one_time_password value="issued_at"]:TheInserts the time the one-time password was generated.[one_time_password value="expires_at"]:TheInserts the time the one-time password expires.
One-time passwords always expire after 15 minutes.
User-Side
This cannot 

If
Using this Feature
User-Side MFA is enabled on the site, a section for multi-factor authentication settings will appear below the password section.Management
ItUsers containscan a status of the user’s current settings,enable and a button that links to the page where settings can be managed.
Clicking on the button at the bottom of the page will open to the multi-factor authentications settings page.
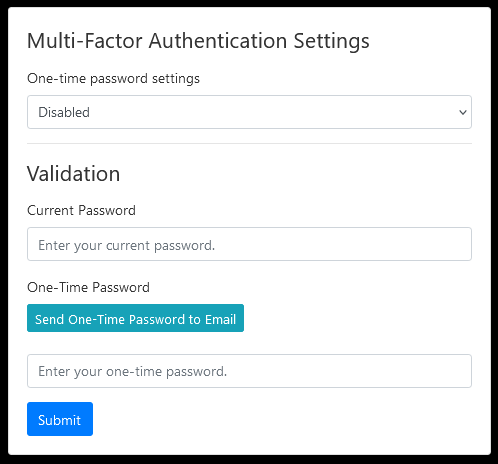
Here, the user can changemanage their MFA settings. Currently, the only options available are to disable MFA, or to use one-time passwords.
In order to save any changes to their settings, the user will need to enter their current password and an initial one-time password.
The user can have a one-time password emailedsettings tofrom their security page (formerly the email address they have on file by clicking the button to send a one-time password to their email.
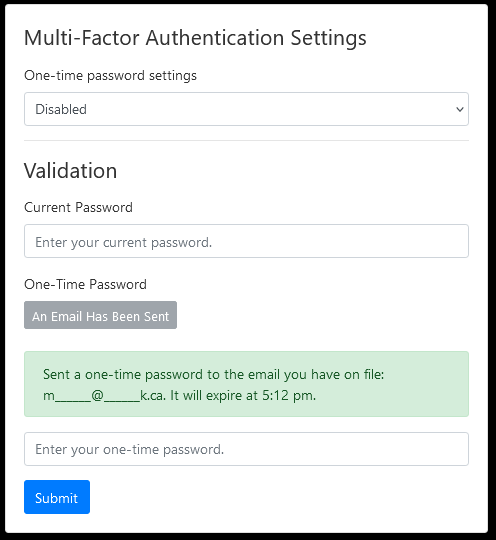
The password is only valid for 15 minutes after the point of generation, at which point it will no longer work if entered. The user will have to generate a new password after it has expired.
When a user generates a new one-time password, any unused passwords they have in the system will be rendered unusable, even if they haven’t expired yet.
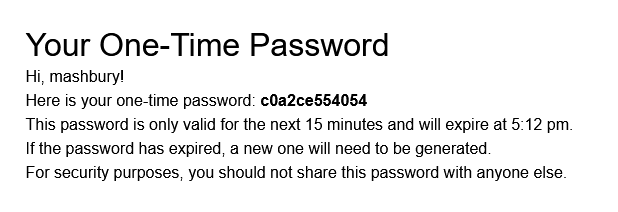
page). An example of a one-time password email.
The email will use the formatting of the template that was set up for one-time passwords.
The one-time password must be entered into the box below the current password box.
By pressing the submit button, the user will now be able to update their MFA settings.
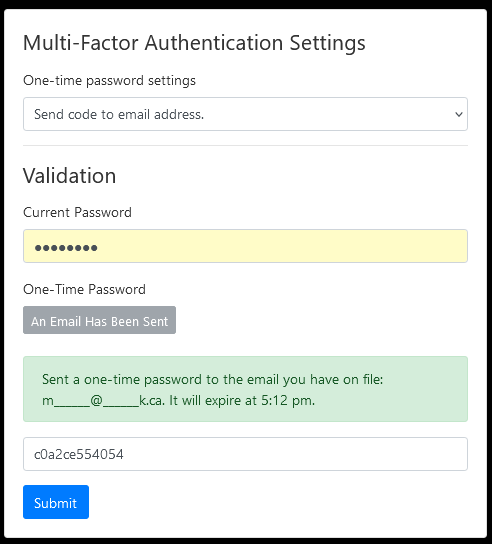
Entering a one-time password.
Logging In
When a user has one-time passwords enabled on their account, they will be prompted after every subsequent regular login to enter a one-time password before they can access the site.
The username and password are entered as normal, then the one-time password screen is shown. The user will be redirectedRefer to this pagewiki whenever they tryarticle to access a page other than one of these:
/login-see theloginstepspage./logout- the logout page./one_time_password- the one-time password enter screen./account/send_email- the one-time password send email endpoint./account/multiauth- the user account multi-auth settings page.
If the user does not have one-time passwords setup on their account but the site has one-time passwords set as required on the site, the user will instead be redirected to the multi-authentication setup page. They will not be able to move away from this page until they complete the setup.
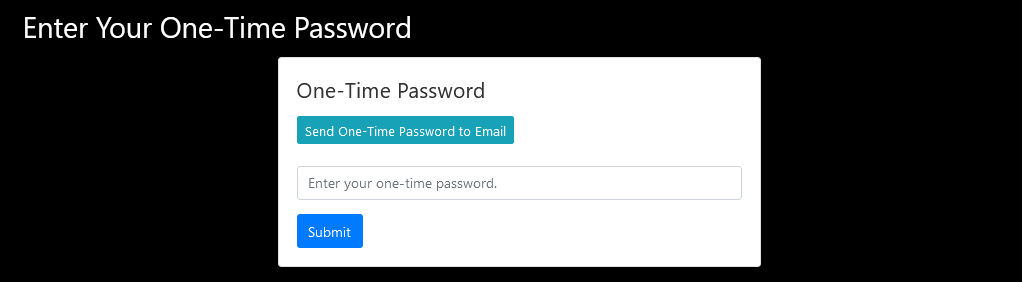
The one-time password screen.
The page works just like the setup, with a button to send a new one-time password to the user’s email address.
After the user enters the one-time password and submits, they will be able to proceed to the rest of the website as normal.involved.
The state of theirthe user's one-time password verification is stored in the local storage of their session data. If the local storage is cleared,cleared (e.g., clearing browser cache), they fillwill have to enter another one-time password.
The dataMFA verification does not persist across different web browsers,browsers or devices, meaning if the user will have to enter a new one-time password if they try to loginlog in using another browser or device.
Best Practices
&
Considerations
- Security

MFA
significantly reduces
- Security Enhancement:

