Configuring Multi-Factor Authentication on the User Portal
Multi-Factor Authentication (MFA) adds a crucial second layer of security to user accounts in OPSCOM, significantly enhancing protection against unauthorized access. Currently, the primary method implemented is the use of one-time passwords (OTPs) sent via email. This article outlines how administrators can configure MFA at the system level and how users interact with this enhanced security feature on their portal.
Setup & Configuration
Implementing MFA involves administrator-side configuration within System Settings and customizing the associated email template.
Admin Side Configuration
One-time passwords will not be available on the user portal until enabled within System Settings.
- Hover over System Configuration and click System Settings.
- On the User Profile tab, click Enable Multi-Factor Authentication.
If this setting is not available for you to change, please have your primary Admin contact support@ops-com.com to have it turned on.
This is a ternary setting, meaning it has three different states, allowing for flexible control over MFA implementation:
Email Template Configuration
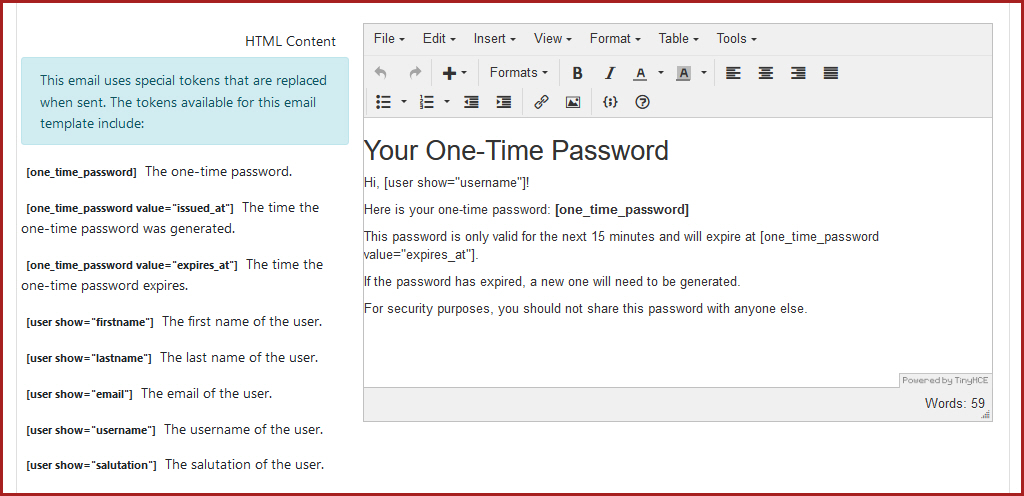
The content of the one-time password email sent to users is defined within a dedicated email template.
- Hover over System Configuration, Content & Designs and click Email Templates.
- Locate and edit the One-Time Password Email Template.
Here, administrators can define the message and branding of the email. In addition to general user-specific shortcodes, this template includes specific shortcodes for OTP details:
[one_time_password]: Inserts the randomly generated one-time password.[one_time_password value="issued_at"]: Inserts the time the one-time password was generated.[one_time_password value="expires_at"]: Inserts the time the one-time password expires.
One-time passwords always expire after 15 minutes. This cannot be changed.
Using this Feature
User-Side MFA Management
Users can enable and manage their one-time password settings from their security page (formerly the passwords page). Refer to this wiki article to see the steps involved.
The state of the user's one-time password verification is stored in the local storage of their session data. If the local storage is cleared (e.g., clearing browser cache), they will have to enter another one-time password. The MFA verification does not persist across different web browsers or devices, meaning the user will have to enter a new one-time password if they try to log in using another browser or device.
Best Practices & Considerations
- Security Enhancement: MFA significantly reduces the risk of unauthorized access, even if primary login credentials are compromised. It is highly recommended for all users.
- Gradual Rollout (Visible vs. Required): When introducing MFA, consider starting with the Visible setting to allow users to opt-in voluntarily. Once accustomed, transition to Required for all users if your security policy mandates it.
- Clear Communication: Inform users about the MFA requirement, how to set it up, and how to log in using OTPs. Provide clear instructions and troubleshooting tips.
- Email Deliverability: Ensure that your system's email settings are correctly configured and that OTP emails are not being blocked by spam filters. Users need to receive these emails promptly to log in.
- Template Customization: Customize the OTP email template to include your organization's branding and any specific instructions for your users.
- User Training: Consider providing brief training or a guide for users on how to manage their MFA settings and log in with OTPs.
- OTP Expiry: Remind users that OTPs are time-sensitive (15 minutes) and that generating a new one invalidates previous ones.
